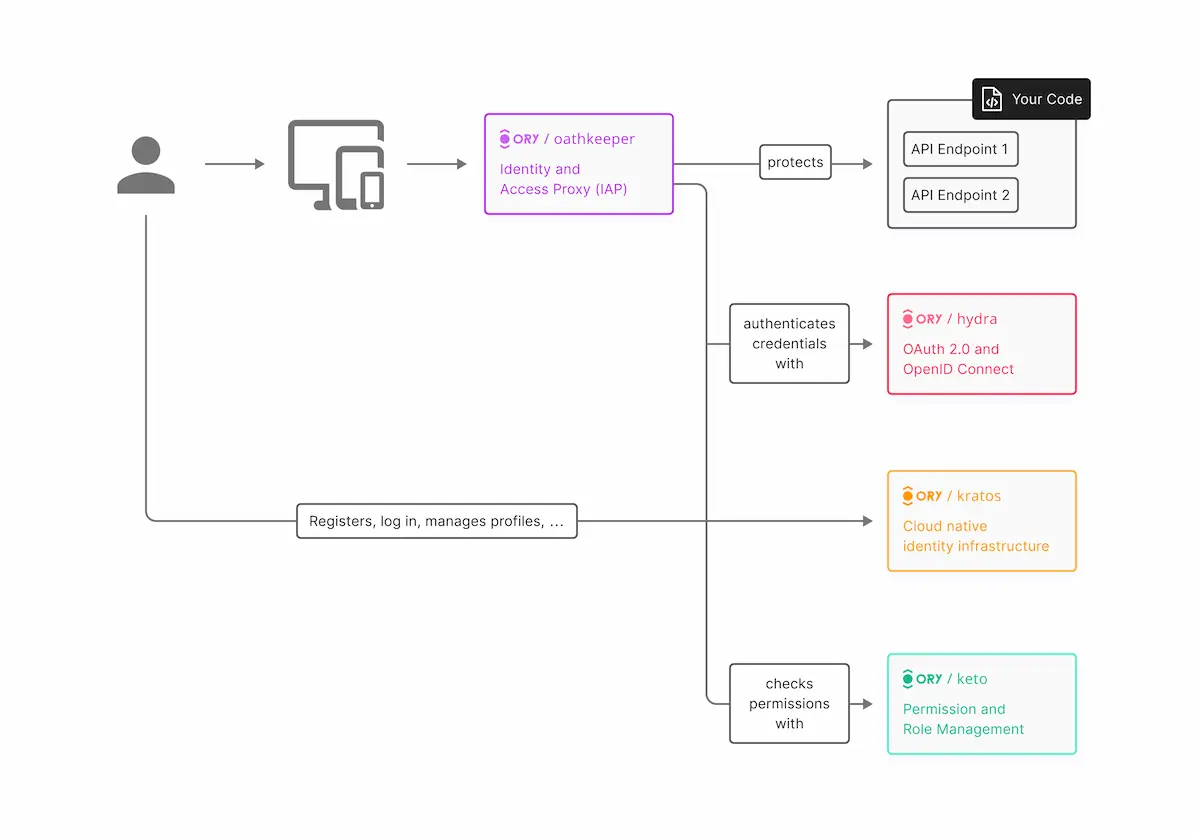
Ory Ecosystem
- Ory Kratos: a new software archetype Identity Infrastructure Service.
- Ory Hydra: an OAuth 2.0 and OpenID Connect Provider.
- Ory Oathkeeper: authorizes incoming HTTP requests.
- Ory Keto: the first and only open source implementation of "Zanzibar: Google's Consistent, Global Authorization System".
Prerequisites
Ory Kratos
Quickstart
git clone -b v0.6.3-alpha.1 --depth 1 https://github.com/ory/kratos.git
cd kratos
docker-compose -f quickstart.yml -f quickstart-standalone.yml up --build --force-recreate
# If you have SELinux, run:
docker-compose -f quickstart.yml -f quickstart-selinux.yml -f quickstart-standalone.yml up --build --force-recreate
- Ory Kratos
- Public ("Browser") API (port 4433)
- Admin API (port 4434) - This is only made public so we can test via the CLI.
- SecureApp
- Public (port 4455) - an example application written in NodeJS that implements the login, registration, logout, dashboard, and other UIs.
- MailSlurper
- Public (port 4436) - a development SMTP server which Ory Kratos will use to send emails.
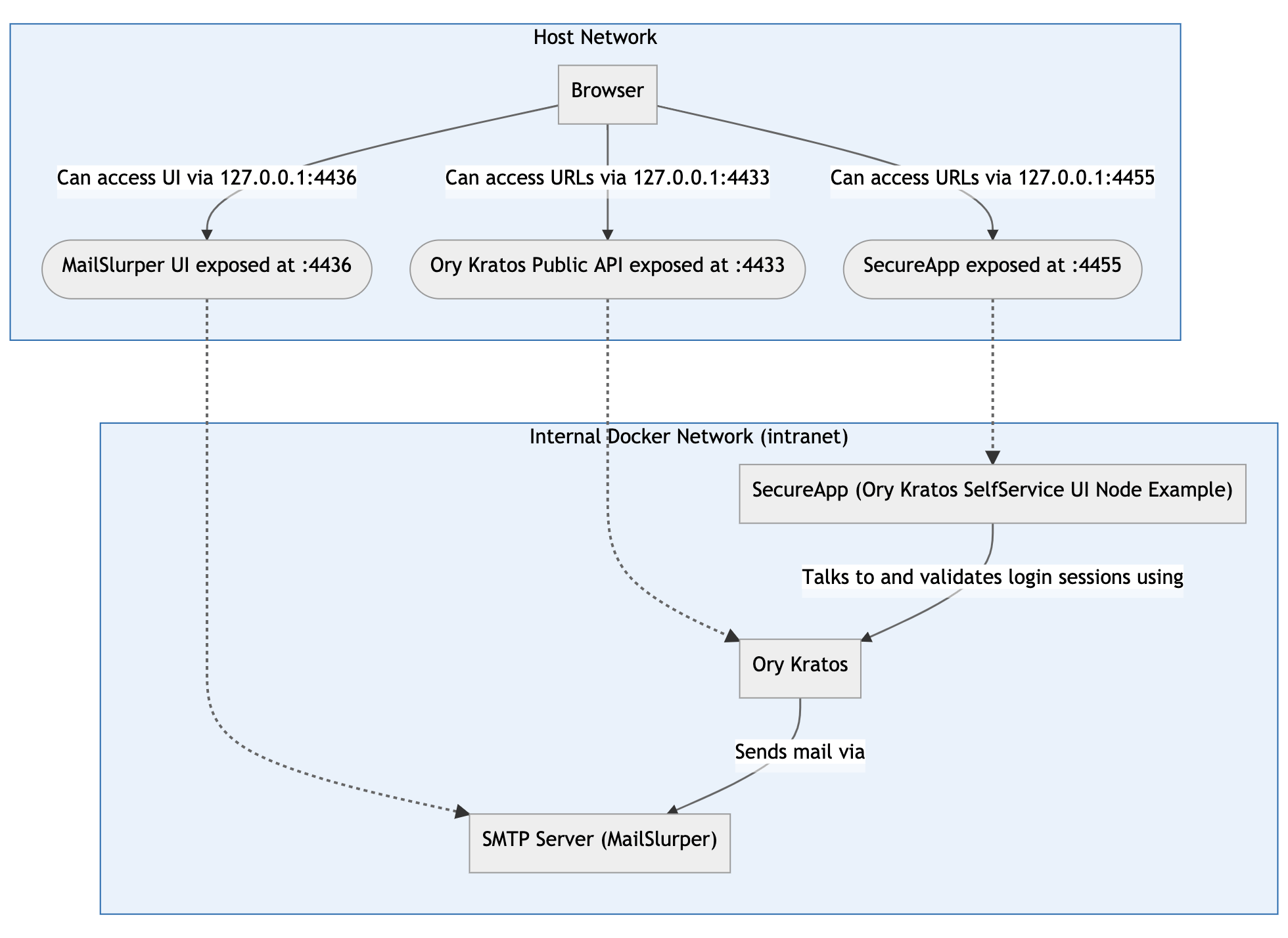
Open http://127.0.0.1:4455/dashboard to experience. After Register new account / Reset password, go to http://127.0.0.1:4436 (fake SMTP server) to retrieve your emails.
Clean up:
docker-compose -f quickstart.yml down -v
docker-compose -f quickstart.yml rm -fsv
Installation
docker pull oryd/kratos:v0.6.3-alpha.1
docker run --rm -it oryd/kratos:v0.6.3-alpha.1 help
Ory Hydra
5 Minute Tutorial
git clone -b v1.10.2 --depth 1 https://github.com/ory/hydra.git
cd hydra
# start the needed containers
docker-compose -f quickstart.yml \
-f quickstart-postgres.yml \
up --build
OAuth 2.0 Client:
# create the OAuth 2.0 Client
$ docker-compose -f quickstart.yml exec hydra \
hydra clients create \
--endpoint http://127.0.0.1:4445/ \
--id my-client \
--secret secret \
-g client_credentials
You should not provide secrets using command line flags, the secret might leak to bash history and similar systems
OAuth 2.0 Client ID: my-client
# perform the client credentials grant
$ docker-compose -f quickstart.yml exec hydra \
hydra token client \
--endpoint http://127.0.0.1:4444/ \
--client-id my-client \
--client-secret secret
58O7jfLge4ZiTTUhxgYO6UIts_p1kiIS-GJ2t0y1NcI.oCpSn6o3Uv92DmS_PpJPcFmdMskrIShJwa5t50FWQ5Y
# perform token introspection on that token
$ docker-compose -f quickstart.yml exec hydra \
hydra token introspect \
--endpoint http://127.0.0.1:4445/ \
58O7jfLge4ZiTTUhxgYO6UIts_p1kiIS-GJ2t0y1NcI.oCpSn6o3Uv92DmS_PpJPcFmdMskrIShJwa5t50FWQ5Y
{
"active": true,
"aud": [],
"client_id": "my-client",
"exp": 1624940427,
"iat": 1624936827,
"iss": "http://127.0.0.1:4444/",
"nbf": 1624936827,
"sub": "my-client",
"token_type": "Bearer",
"token_use": "access_token"
}
OAuth 2.0 Authorization Code Grant:
# create a client that is capable of performing that grant
$ docker-compose -f quickstart.yml exec hydra \
hydra clients create \
--endpoint http://127.0.0.1:4445 \
--id auth-code-client \
--secret secret \
--grant-types authorization_code,refresh_token \
--response-types code,id_token \
--scope openid,offline \
--callbacks http://127.0.0.1:5555/callback
You should not provide secrets using command line flags, the secret might leak to bash history and similar systems
OAuth 2.0 Client ID: auth-code-client
# start a server that serves an example web application: http://127.0.0.1:5555
$ docker-compose -f quickstart.yml exec hydra \
hydra token user \
--client-id auth-code-client \
--client-secret secret \
--endpoint http://127.0.0.1:4444/ \
--port 5555 \
--scope openid,offline
Setting up home route on http://127.0.0.1:5555/
Setting up callback listener on http://127.0.0.1:5555/callback
Press ctrl + c on Linux / Windows or cmd + c on OSX to end the process.
If your browser does not open automatically, navigate to:
http://127.0.0.1:5555/
open the URL http://127.0.0.1:5555,
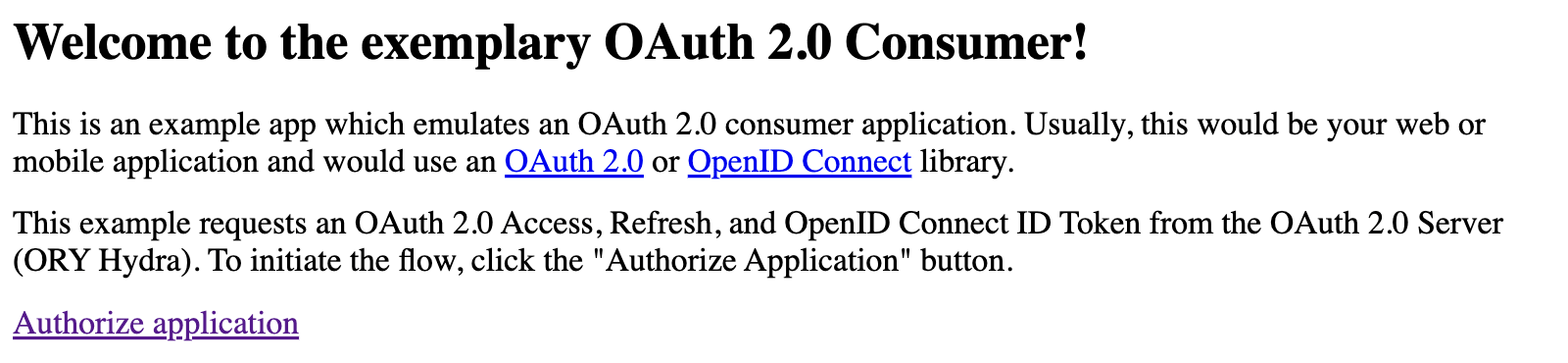
log in,

authorize the application,
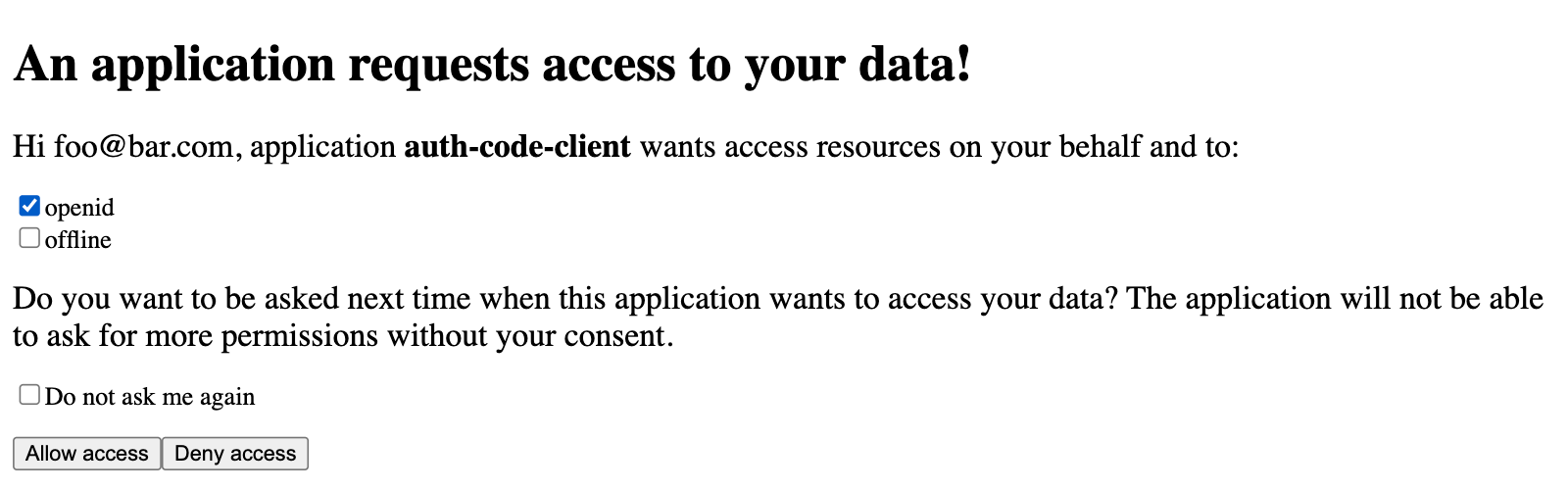
see access token in the response,
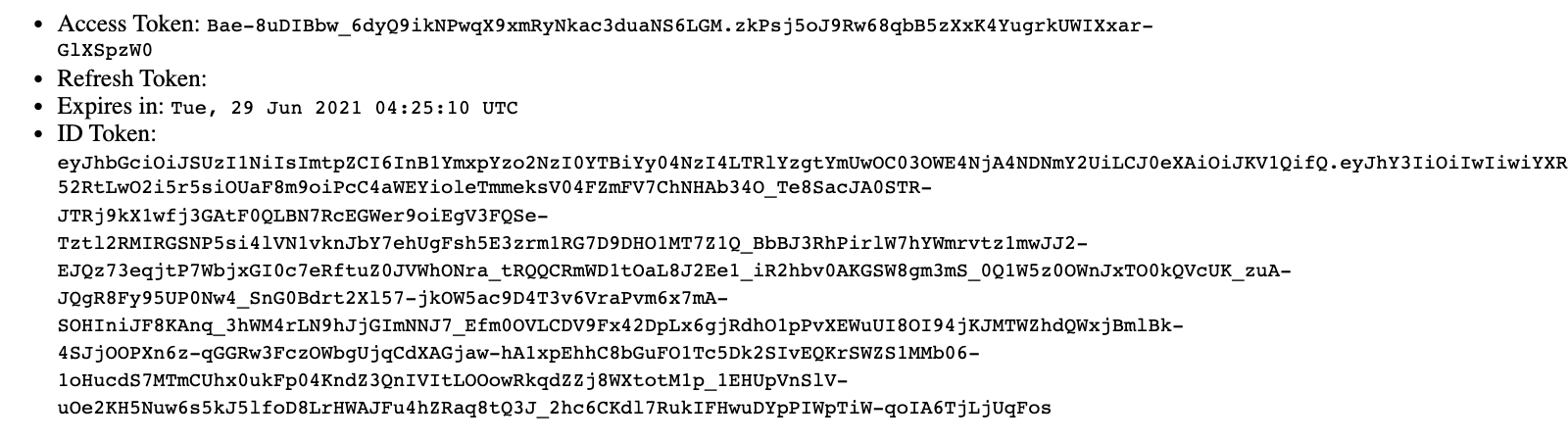
Access Token:
Bae-8uDIBbw_6dyQ9ikNPwqX9xmRyNkac3duaNS6LGM.zkPsj5oJ9Rw68qbB5zXxK4YugrkUWIXxar-GlXSpzW0
Refresh Token:
Expires in:
Tue, 29 Jun 2021 04:25:10 UTC
ID Token:
eyJhbGciOiJSUzI1NiIsImtpZCI6InB1YmxpYzo2NzI0YTBiYy04NzI4LTRlYzgtYmUwOC03OWE4NjA4NDNmY2UiLCJ0eXAiOiJKV1QifQ.eyJhY3IiOiIwIiwiYXRfaGFzaCI6IldaNlQ3UUo0SGlNaWZTc0pOS1VZM0EiLCJhdWQiOlsiYXV0aC1jb2RlLWNsaWVudCJdLCJhdXRoX3RpbWUiOjE2MjQ5MzcwNDMsImV4cCI6MTYyNDk0MDcxMSwiaWF0IjoxNjI0OTM3MTExLCJpc3MiOiJodHRwOi8vMTI3LjAuMC4xOjQ0NDQvIiwianRpIjoiOGE1MGRlM2YtMjMwNi00ZjIwLWExOGYtODE2MjlkOThmODQyIiwibm9uY2UiOiJsY2x1dndxc2FuaGlrZGd2anFrcHh4c2UiLCJyYXQiOjE2MjQ5MzcwMTYsInNpZCI6ImFhZDg3NmI2LTZlZTAtNGFmNC1hYzNkLWY2MzhhZTJhNDdjMSIsInN1YiI6ImZvb0BiYXIuY29tIn0.DlZ-52RtLwO2i5r5siOUaF8m9oiPcC4aWEYioleTmmeksV04FZmFV7ChNHAb34O_Te8SacJA0STR-JTRj9kX1wfj3GAtF0QLBN7RcEGWer9oiEgV3FQSe-Tztl2RMIRGSNP5si4lVN1vknJbY7ehUgFsh5E3zrm1RG7D9DHO1MT7Z1Q_BbBJ3RhPirlW7hYWmrvtz1mwJJ2-EJQz73eqjtP7WbjxGI0c7eRftuZ0JVWhONra_tRQQCRmWD1tOaL8J2Ee1_iR2hbv0AKGSW8gm3mS_0Q1W5z0OWnJxTO0kQVcUK_zuA-JQgR8Fy95UP0Nw4_SnG0Bdrt2Xl57-jkOW5ac9D4T3v6VraPvm6x7mA-SOHIniJF8KAnq_3hWM4rLN9hJjGImNNJ7_Efm0OVLCDV9Fx42DpLx6gjRdhO1pPvXEWuUI8OI94jKJMTWZhdQWxjBmlBk-4SJjOOPXn6z-qGGRw3FczOWbgUjqCdXAGjaw-hA1xpEhhC8bGuFO1Tc5Dk2SIvEQKrSWZS1MMb06-1oHucdS7MTmCUhx0ukFp04KndZ3QnIVItLOOowRkqdZZj8WXtotM1p_1EHUpVnSlV-uOe2KH5Nuw6s5kJ5lfoD8LrHWAJFu4hZRaq8tQ3J_2hc6CKdl7RukIFHwuDYpPIWpTiW-qoIA6TjLjUqFos
http: Server closed
Clean up:
docker-compose -f quickstart.yml kill
docker-compose -f quickstart.yml rm -f -v
Installation
docker pull oryd/hydra:v1.10.2
docker run --rm -it oryd/hydra:v1.10.2 help
Ory Oathkeeper
Installation
docker pull oryd/oathkeeper:v0.38.12-beta.1
docker run --rm -it oryd/oathkeeper:v0.38.12-beta.1 help
Ory Keto
Quickstart
git clone -b v0.6.0-alpha.3 --depth 1 https://github.com/ory/keto.git
cd keto
$ docker-compose -f contrib/cat-videos-example/docker-compose.yml up
keto-init_1 | NAMESPACE OBJECT RELATION NAME SUBJECT
keto-init_1 | videos /cats/1.mp4 owner videos:/cats#owner
keto-init_1 | videos /cats/1.mp4 view videos:/cats/1.mp4#owner
keto-init_1 | videos /cats/1.mp4 view *
keto-init_1 | videos /cats/2.mp4 owner videos:/cats#owner
keto-init_1 | videos /cats/2.mp4 view videos:/cats/2.mp4#owner
keto-init_1 | videos /cats owner cat lady
keto-init_1 | videos /cats view videos:/cats#owner
Simulating the Video Sharing Application:
alias keto="docker run -it --network cat-videos-example_default -e KETO_READ_REMOTE=\"keto:4466\" oryd/keto:v0.6.0-alpha.3"
Check Incoming Requests:
# Is "*" allowed to "view" the object "videos":"/cats/2.mp4"?
$ keto check "*" view videos /cats/2.mp4
Denied
# Who is allowed to "view" the object "videos":"/cats/2.mp4"?
$ keto expand view videos /cats/1.mp4
∪ videos:/cats/1.mp4#view
├─ ☘ *️
├─ ∪ videos:/cats/1.mp4#owner
│ ├─ ∪ videos:/cats#owner
│ │ ├─ ☘ cat lady️
# Is "*" allowed to "view" the object "videos":"/cats/1.mp4"?
$ keto check "*" view videos /cats/1.mp4
Allowed
Installation
docker pull oryd/keto:v0.6.0-alpha.3
docker run --rm -it oryd/keto:v0.6.0-alpha.3 help